How to examine if your computer is infected, if your PC is a part of a botnet or some hacker has unauthorized access to your computer through a remote administration tool or your computer is infected by some kind of trojan which is giving out your personal information to the hacker.
If your computer is infected and you are connected to the internet then you wouldn’t even know what information is going out from your computer to the hacker who could sitting in any part of the world. The info might be your login username and password, credit card info or anything else.
Some of the newest viruses and trojans can even go undetected if the Antivirus systems have not yet been updated to detect and remove the infection.
Many cyber thieves, hackers and script kiddies use tools known as Crypters which can make a trojan or other malicious programs undetectable by security products such as Antivirus. Some crypters are fee some are paid versions, some of them are really effective and can completely make malicious programs undetectable by Antivirus software. So just because you have an antivirus installed doesn’t mean your PC can’t get infected, the best practice is to never download any file from an unknown source.
Here are a few things you can do to examine if your computer is infected or not.
Internet connection can serve as a medium between your and the hacker’s computer through which the communication takes place in the background in case your PC is infected, therefore you need to check the network connections, whether your PC is connected to some unknown or suspicious host, IP or domain name.
Run Command Prompt in Administrator mode
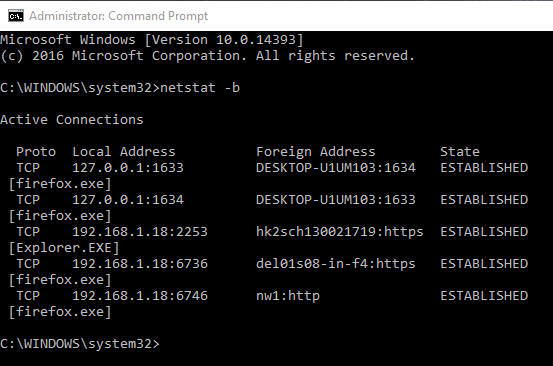
Run the command
netstat -b
Here we see a bunch of connections running, first one is 127.0.0.1 which is local host and then we have firefox.exe and Explorer.exe
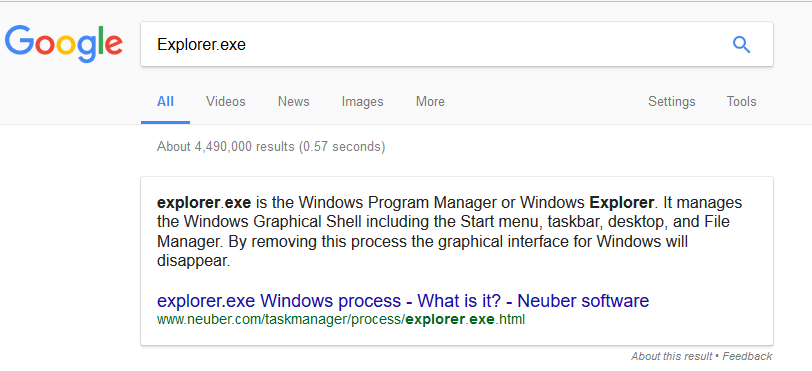
You may see more processes / application-name.exe depending on the number of applications you might be running at the time when you use this command. Here you should look for the .exe process which looks unknown or suspicious to you. Then search it on google.
Google shows Explorer.exe is a windows process and completely safe. If you find anything suspicious then search it on google and you would come to know if it is a legitimate process or some malicious program.
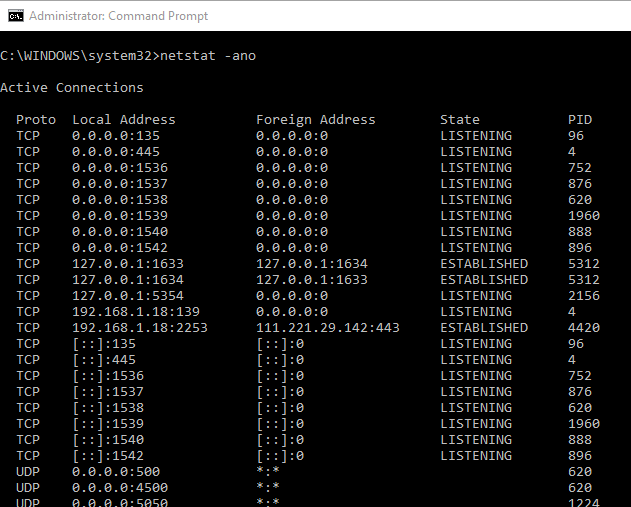
Next run the command
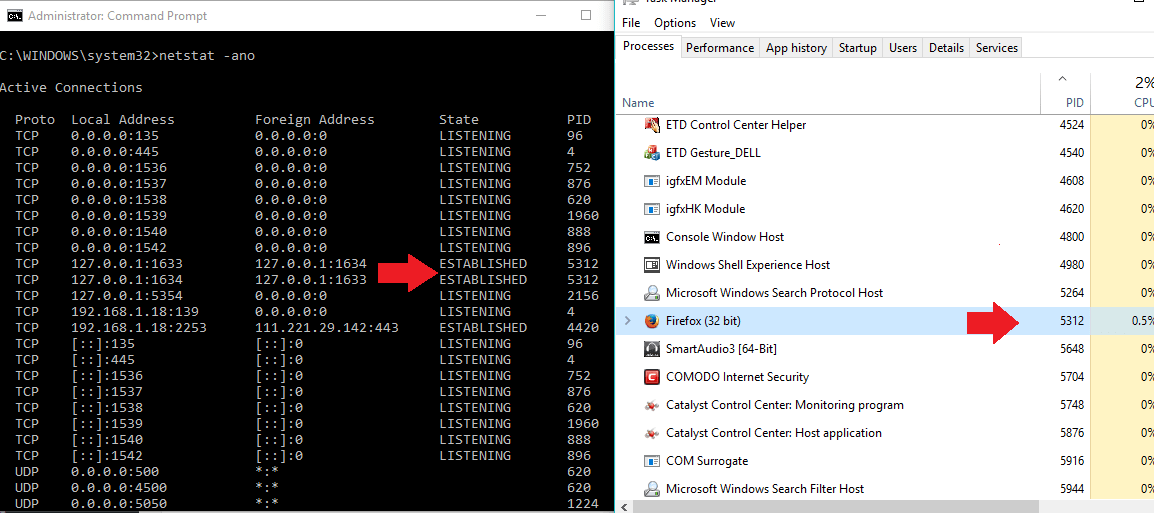
netstat -ano
Focus on the connections whose state is “Established” under the state column
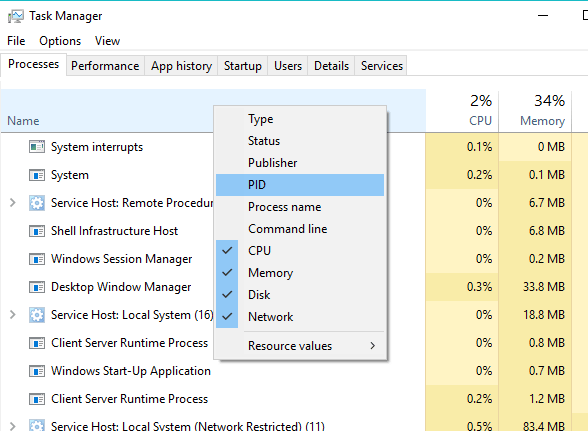
Open the Task Manager (short cut Press Ctrl+Alt+Del )
Add PID column to the task manager if you don’t have it.
To do so move your mouse cursor over the name column then right click and then click on PID.
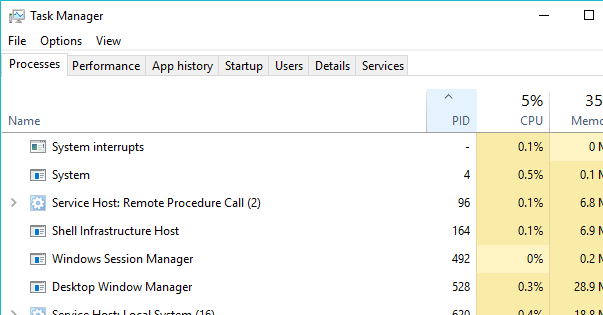
Click on the PID column to arrange the processes according to their PIDs
Now figure out which process is using the connection ? (You should look for the ones whose state is ‘Established’ ).
Match the PID with the PID in the Task Manager and it turns out to be firefox.exe (5312) in this example, which is a safe application.
A malicious program can be named after a genuine process like firefox.exe, explorer.exe to make it seem like an authentic process in that case firefox.exe would have 2 different PID’s and you can spot the fake one by checking its digital signature.
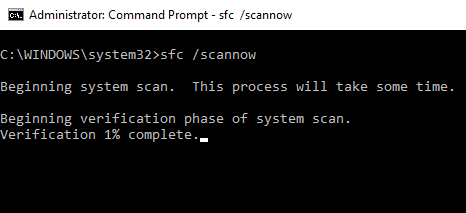
Use the command
sfc /scannow
This command checks the integrity of the system files. A malware can embed itself into the system files which may go undetected.
Make use of Wireshark.
Wireshark is a famous tool used to analyze packets / network connections.
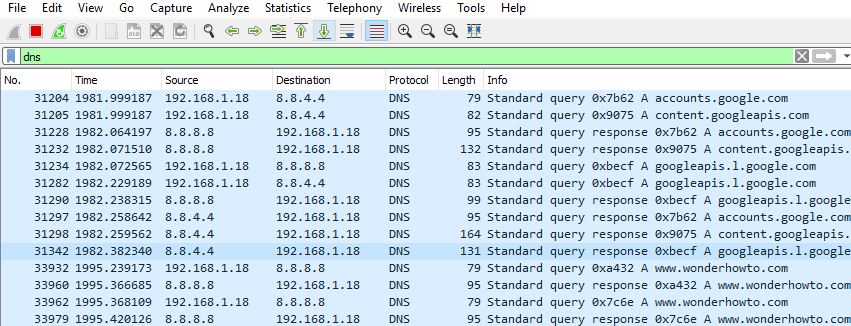
In the filter box type dns and it will filter out and show all the connections making use of DNS. If you have opened up many web pages in your browser then it will show connection details of every one of them. The idea here is to check for suspicious connections and it can be challenging. There could be a very long list of these DNS rows you might have to go through so I suggest you do to either close your browser or do not open more than one web page while running this test. Additionally if you are running any other application that uses the internet like a game client then close that down too.
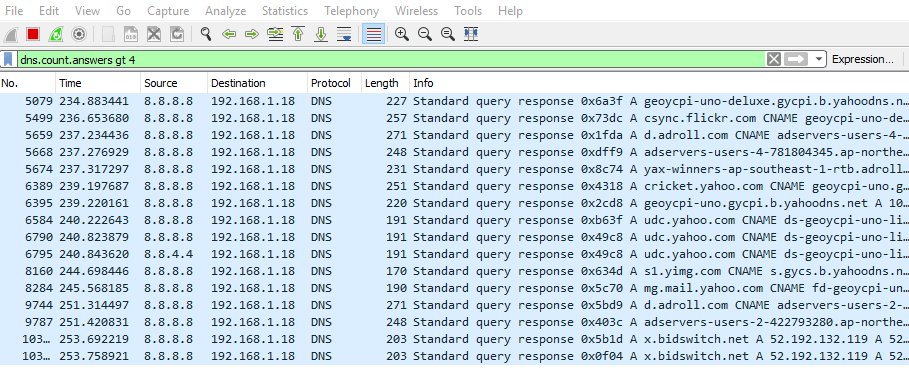
If the list of DNS rows are too long for you to go though all of them then use the command to filter out the and display only those connections which have used more than 4 answer requests because usually high amount of answer requests takes place in case of a malicious connection.
dns.count.answers gt 4
Put this command into the filter box and hit enter
Here we need to examine if the computer is connecting to some suspicious domains, hosts or IP. In the above pic see for example in the second row under the info column csync.flickr.com. Flicker.com is a safe domain its a legitimate website so no problem there. Look for anything that raises suspicion.
Lets see adservers-users-2, third one from the end.
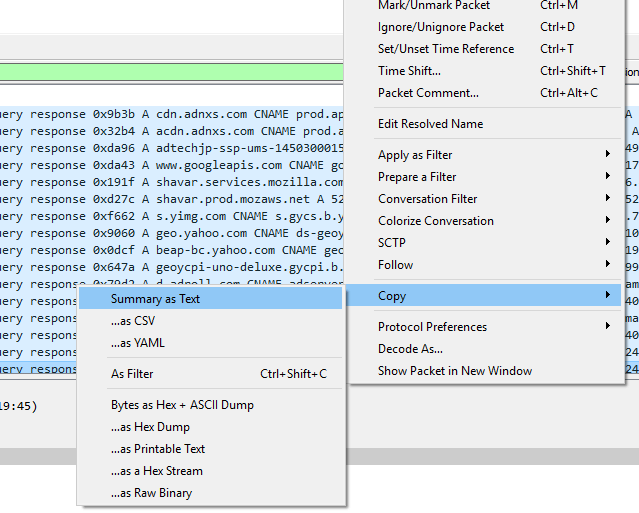
Right click on it then go to copy and click on “summary as text”.
Paste it in the notepad or anywhere else and copy the full domain name including the sub-domain which in this case was adservers-users-2-422793280.ap-northeast-1.elb.amazonaws.com
Search the entire name on google as well as search it without the sub-domain on google (amazonaws.com is domain name without the subdomin).
You would come to know that amazonaws is Amazon Web Services which is a part of Amazon and is very safe. So this is how you can examine if your PC is connected to a legitimate host or if there is some malicious program which is establishing a connection with an unknown or suspicious host which has been reported as malicious in nature.
You can also check if the domain has been blacklisted using the following site http://mxtoolbox.com/blacklists.aspx
In the protocol column look for unusual protocols such as IRC, TFTP, SSH. If you find one then the traffic associated with it should be seen with suspicion especially when you are not running any application which makes use of those protocols.
Under statistics click on protocol hierarchy
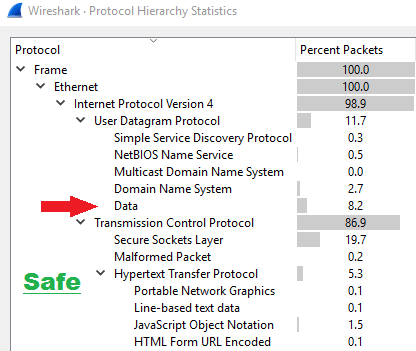
Now look for “Data”
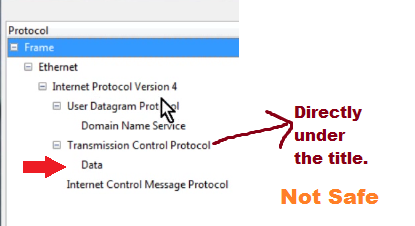
“Data” should not be directly below the Title / Heading as you may see in the example below.
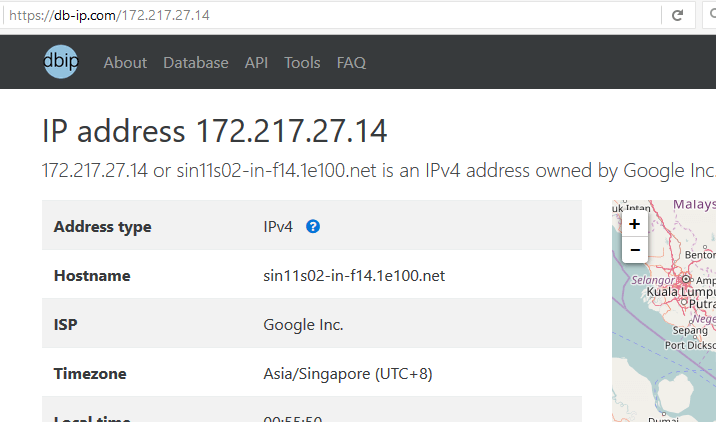
If the “Data” is directly below one of the headings then it should be a big warning sign. If that is the case then right click on the “Data” and then you can find the traffic associated with that data. Search the IP address to which it is connecting whether it is safe or not. You can check the IP address using https://db-ip.com or http://whatismyipaddress.com/ip-lookup
It is safe if the IP belongs to companies like microsoft, google etc.. but if the IP is from an “internet service provider” for example google fiber or any other ISP then it could belong to anyone. It could be the IP address of the computer which has unauthorized access to your PC.
You can also check whether the suspicious IP address or domain name is blacklisted using this website http://mxtoolbox.com/blacklists.aspx
Wireshark is an advanced and sophisticated tool it has a certification named Wireshark Certified Network Analyst (WCNA) and one cannot learn it in a single day these were just a few tips on how to use it to examine if your PC is infected by some malware.